SMS Blog
Zero Trust Microsegmentation with Illumio Core
Trust Issues
Every day, we are bombarded with news of cyber security breaches and ransomware attacks that cost companies a fortune and compromise sensitive data. It’s not a matter of if, but when your boundary is breached. The legacy firewall network segmentation methodology, known as castle-and-moat, was not designed to stop the spread of a breach once the moat is crossed. Once one workload within your network boundary is compromised, bad actors and malware can spread rapidly and uninhibited.
In May 2021, the Executive Order (EO) 14028, titled ‘Improving the Nation’s Cybersecurity,’ was issued. This order mandates the adoption of a Zero Trust Architecture (ZTA) within the US Government. The order defines that a ZTA security model operates under the assumption that a breach is inevitable or has likely already occurred.
Microsegmentation
Microsegmentation is a foundational component of a ZTA. It helps contain a breach by moving the boundary to the workloads where the data originates. In the Department of Defense’s (DoD) Zero Trust Strategy, which outlines seven pillars essential for achieving a ZTA, microsegmentation is highlighted as a key component of the ‘Network & Environment’ pillar. Additionally, it also significantly contributes to the success of other pillars, such as ‘Applications & Workloads’ and ‘Visibility & Analytics’.
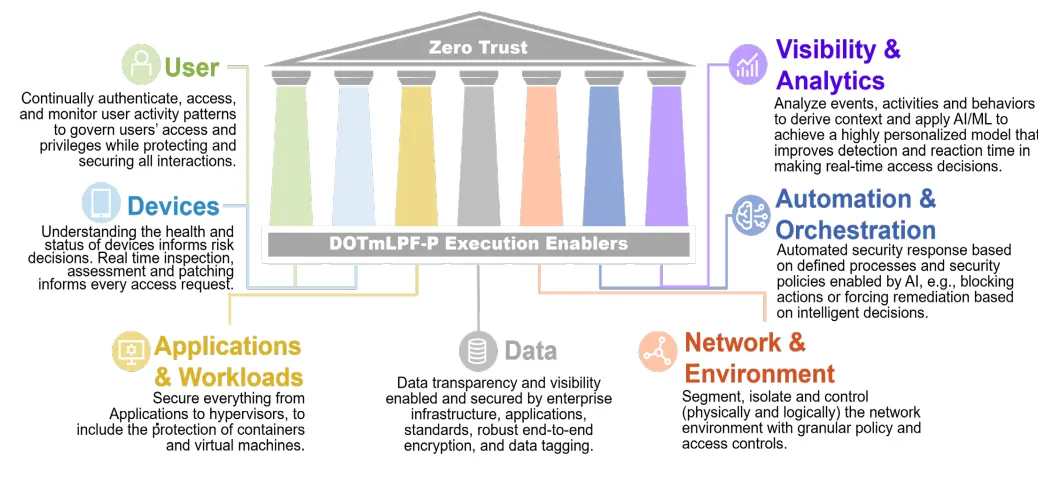
One of the first steps and core capabilities of microsegmentation is flow mapping. Data flows are collected from all devices and are then visualized within a web UI. Once organizations have visibility of the current state of their workload’s flows, they can move toward updating their policies to an allow-list model.
An allow-list model explicitly permits only necessary traffic and denies all other traffic implicitly, following the principle of least privilege. By restricting access to only what is essential, microsegmentation ensures that any breach is not only contained but also quickly identified and eliminated.
Illumio Core
In the following sections, I will provide a high-level overview of Illumio Core, Illumio’s approach to segmenting workloads in on-premise and cloud data centers. While Illumio is a key player in this domain, other notable vendors in microsegmentation include Akamai Guardicore, VMware NSX, and Cisco Secure Workload (formerly known as Tetration). Although this piece won’t compare these vendors, a future blog may delve into an analysis of alternatives. Below, you’ll find a company overview of Illumio as provided by the vendor.
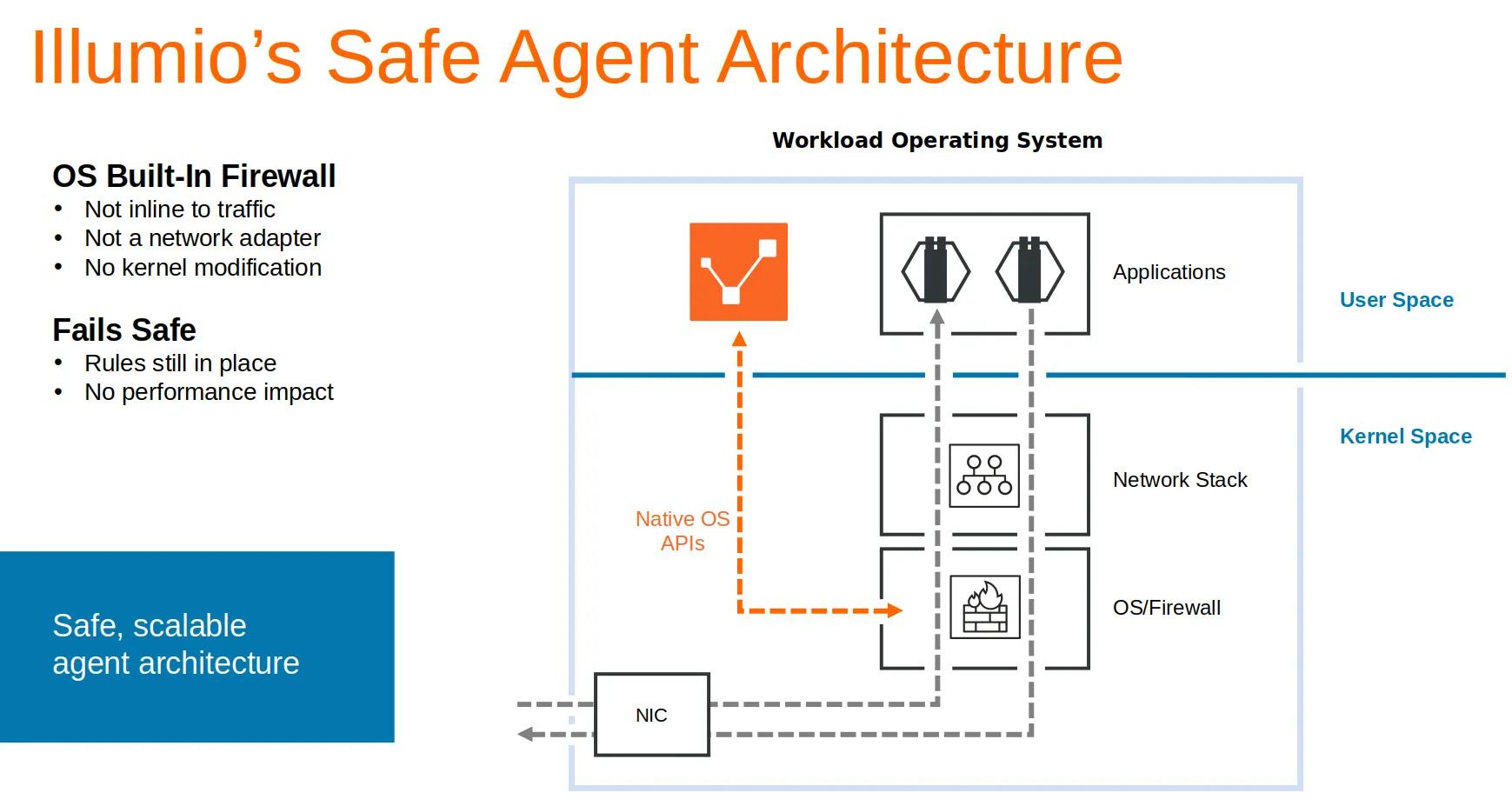
Illumio Core consists of two key components, the Policy Compute Engine (PCE) and the Virtual Enforcement Node (VEN). The PCE is the server side of the platform aka “the brain” and the VEN is the agent that gets installed on workloads converting them to “managed workloads”.

After a VEN is installed on a workload, the VEN can manage the native host’s OS firewall and report all flows in and out of the workload back to the PCEs. Once VENs are deployed throughout the network the PCEs will have full visibility of flows through its web UI. The infographic below shows how the agent is integrated with the host OS.
VEN Enforcement Modes
There are four different enforcement modes a VEN can be set to. It is recommended that VENs are first paired in Idle mode and progressed through the enforcement modes as flows are discovered, rules are created, and policies are enforced.
Idle: The VEN doesn’t take control of the workload’s iptables (Linux) or Windows Firewall (Windows Filtering Platform) yet. The VEN reports the equivalent of a netstat back to the PCEs. A compatibility check is performed to see if there are any incompatibilities with the VEN software.
Visibility Only: The VEN takes full control of the host OS firewall. An allow-all rule is added at the end of the firewall rules so nothing is blocked. The VEN reports all flows back to the PCEs.
Selective Enforcement: Policies created on the PCEs are provisioned. Specific deny rules are added above the allow any/any rule. All flows that do not have implicit allow rules will be logged as “potentially blocked” to help prepare for Full Enforcement mode.
Full Enforcement: Rules are enforced for all inbound and outbound services. Traffic that is not allowed by a rule is blocked.
The Power of Labels
Illumio uses a multi-dimensional label-based model to label workloads, create policies, and grant role-based access control for administrative access. By utilizing labels, policies will dynamically update when IP addresses change, new devices are deployed, or a device is decommissioned.
Illumio recommends four label types by default (Role, Application, Environment, and Location), with the option to create additional custom label types if needed. It’s important to define a labeling schema that is thoughtful, scalable, standardized, and simple.
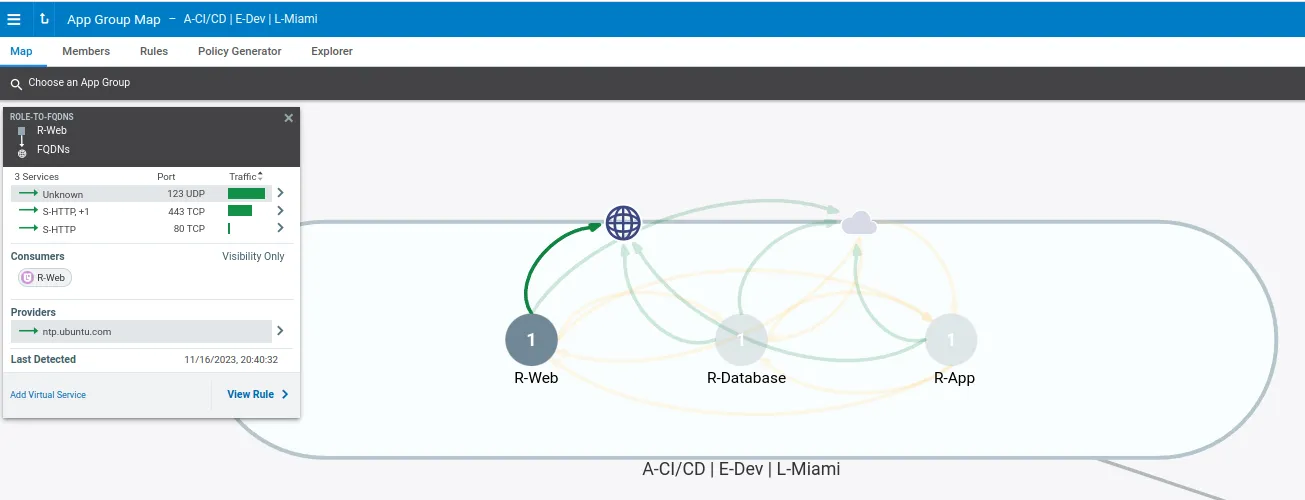
As an example of labeling a workload, an application called CI/CD, could consist of three servers with three different roles: a web server, an application server, and a database server. These servers could be in the development environment and located in Miami. The three workloads within that app group could be labeled as followed:
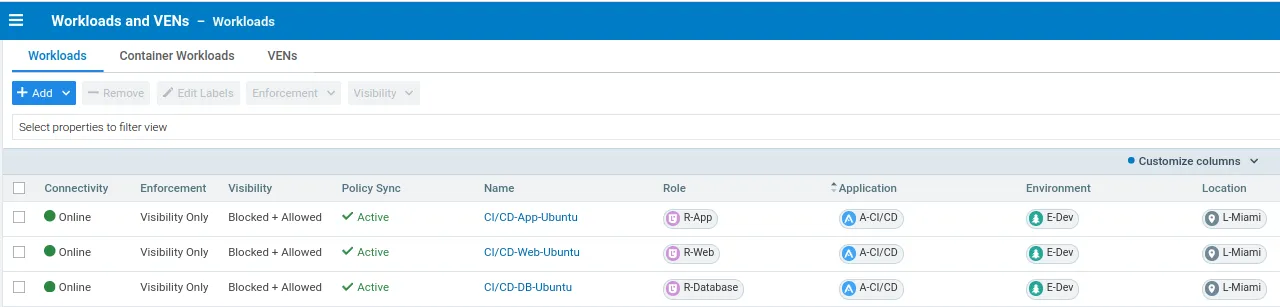
Policy Creation
Once the VENs are deployed and the workloads are labeled it’s time for policy creation. Many application owners don’t know all the flows their application actually needs, especially for east/west traffic that doesn’t leave the network boundary. Historically this has led to either creating weak policies or a broken application until needed ports can be identified.
To overcome this problem, in addition to flow visibility, Illumio provides the ability to draft and test policy before implementation. Illumio will track all flows that would have been blocked if a drafted policy is enforced. Potentially blocked traffic can then be analyzed and rules added before enforcing the policy.
There are many approaches to policy creation and each organization will have different needs. Illumio identifies three segmentation strategies that progressively provide increased security. These strategies allow organizations to progress over time to limit the application attack surface.
Environment or Location Segmentation
Denies traffic from one environment to another, or one location to another. For example, deny all traffic between the development and production environment.
Application Microsegmentation (Ringfencing)
Creates a boundary around applications allowing only necessary ports and protocols in and out of the app group, but allows full communications within the application.
Tier-to-Tier Microsegmentation
Locking down the application further, using role labels, specific tiers/roles can communicate on all ports and protocols within an app group, while blocking unnecessary tier-to-tier communication.
Nanosegmentation
And finally, using role labels and services, specific workloads can communicate only on specific ports.
Each strategy provides a tailored approach to segmentation that can be combined, catering to different organizational needs and security objectives.
Beyond Illumio Core
Besides Illumio Core, Illumio has been expanding its product line to provide a robust microsegmentation solution. Check out the following products to learn more.
Illumio CloudSecure: Agentless segmentation for cloud-native workload.
Illumio Endpoint: Segmentation for end user devices.
Illumio for Microsoft Azure Firewall: Simplify Azure Firewall management with enhanced visibility and Zero Trust security policies.
Bottom Line At The End
In summary, this blog shed light on the critical ‘why’ behind microsegmentation: traditional network segmentation methods are increasingly inadequate in safeguarding data and thwarting ransomware attacks, necessitating a shift in strategy. We delved into ZTA and emphasized the crucial role microsegmentation plays in fulfilling these stringent security requirements. Finally, we provided a high-level overview of Illumio’s solution as a concrete example of microsegmentation in action, illustrating how innovative approaches can effectively respond to modern cybersecurity challenges.
References
Executive Order (EO) 14028, Improving the Nation’s Cybersecurity
https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/
Department of Defense (DoD) Cybersecurity Reference Architecture
https://dodcio.defense.gov/Portals/0/Documents/Library/CS-Ref-Architecture.pdf
Department of Defense (DoD) Zero Trust Strategy
https://dodcio.defense.gov/Portals/0/Documents/Library/DoD-ZTStrategy.pdf
Illumio Resource Center
https://www.illumio.com/resource-center/illumio-core-the-power-of-labels
https://www.illumio.com/resource-center/zero-trust-segmentation-for-dummies

